Device identity and management architecture
If you are planning to manage your devices via EntraID in the clud in the future, there are some architectural decisions to be made in the area of device identity, device management and the type and manner of synchronization tools and methods.
I will try to summarize the main decision paths as briefly as possible to give you an idea or a recommendation for this planning.
Choose the right EntraID device identity
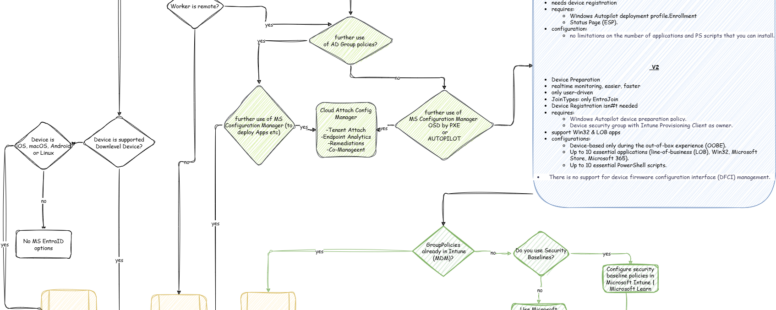
From the point of view that cloud migration is intended to ensure that devices can be installed and managed from anywhere, it is advisable to jump on this bandwagon right away and prefer an EntraID (Only) identity to a hybrid identity if possible and cut off old habits such as AD and Configuration Manager.
TIP: In most cases, I would recommend an on-prem infrastructure hybrid to be integrated into EntrID. And new devices (after a POC) can only be integrated into EntraID (only) with AutoPilot.
However, this requires that all necessary GPOs have previously been transferred to Intune as Device Configuration policies including SecurityBaselines and that these guidelines are applied to the devices. In addition, application delivery and OS deployment via Intune with Autopilot must be ensured. If this cannot be guaranteed, you are better off with a HybridJoin even for new devices. In addition, the configuration manager can connect to Intune and share individual workloads with Intune (cloud attach with co-management). In any case, you should still perform the policiy, OSD, app migrations to Intune as soon as possible. After all, the goal should be to get by with as few on-prem resources as possible and to be able to manage and install a client anywhere (and that without a direct on-prem connection: LAN / VPN).
Excellen blog post: To AAD Join or Not … That is the Question | Microsoft Community Hub
| Scenario | Microsoft Entra join or Hybrid Microsoft Entra join |
|---|---|
| new Windows endpoints |
✔️ Microsoft Entra join |
| ❌ Hybrid Microsoft Entra join Using Hybrid Microsoft Entra Join for new endpoints is possible, but generally not recommended. This might limit the use of modern features in Windows 10/11. |
|
| You have existing, endpoints that are hybrid Microsoft Entra or AD joined |
✔️ Hybrid Microsoft Entra join |
| ❌ Microsoft Entra join Existing devices connected to an on-premises AD domain (including Hybrid Microsoft Entra joined) would need to be reset to switch to Microsoft Entra Join. If resetting is not feasible, there is no supported Microsoft path for converting them to Microsoft Entra Join. |
What are the benefits of Hybrid Azure AD Join?
Device Management
The term device management refers to both the policies (GPOs) that are used to control and protect the device and a system management tool that is responsible for OSD, inventory, app depoymet. In the on-prem world, the AD (GPOs) are used for this purpose in conjunction with a system management tool such as MS Configuration Manager. The counterpart in the cloud is EntraID and Intune.
Device Identity
The identity is differentiated in EntraID:
- Registered:
Microsoft Entra registered Description Definition Registered to Microsoft Entra ID without requiring organizational account to sign in to the device Primary audience Applicable to all users with the following criteria: - Bring your own device
- Mobile devices
Device ownership User or Organization Operating Systems - Windows 10 or newer
- macOS 10.15 or newer
- iOS 15 or newer
- Android
- Linux editions:
- Ubuntu 20.04/22.04 LTS
- Red Hat Enterprise Linux 8/9 LTS
Provisioning - Windows 10 or newer – Settings
- iOS/Android – Company Portal or Microsoft Authenticator app
- macOS – Company Portal
- Linux – Intune Agent
Device sign in options - End-user local credentials
- Password
- Windows Hello
- PIN
- Biometrics or pattern for other devices
Device management - Mobile Device Management (example: Microsoft Intune)
- Mobile Application Management
Key capabilities - Single sign-on (SSO) to cloud resources
- Conditional Access when enrolled into Intune
- Conditional Access via App protection policy
- Enables Phone sign in with Microsoft Authenticator app
- EntraID Joined:
Microsoft Entra join Description Definition Joined only to Microsoft Entra ID requiring organizational account to sign in to the device Primary audience Suitable for both cloud-only and hybrid organizations. Applicable to all users in an organization Device ownership Organization Operating Systems All Windows 11 and Windows 10 devices except Home editions Windows Server 2019 and newer Virtual Machines running in Azure (Server core isn’t supported) (Public preview) Apple devices running macOS 13 or newer Provisioning Self-service: Windows Out of Box Experience (OOBE) or Settings Bulk enrollment Windows Autopilot (Public preview) Apple Automated Device Enrollment (applies to Apple devices only) Device sign in options Organizational accounts using: Password Passwordless options like Windows Hello for Business, Platform Credential for macOS (Public preview) and FIDO2.0 security keys. Device management Mobile Device Management (example: Microsoft Intune) Configuration Manager standalone or co-management with Microsoft Intune Key capabilities single sign-on (SSO) to both cloud and on-premises resources Conditional Access through mobile device management (MDM) enrollment and compliance evaluation Self-service Password Reset and Windows Hello PIN reset on lock screen With an EntraIDJoin, the following considerations must be made regarding on-prem access:
-
-
- On-premises web applications: for SSO and Windows authentication to work, you need to add the URLs to the trusted sites
- On-premises applications: using legacy protocols: Users get single sign-on from Microsoft Entra joined devices if the device has access to a domain controller: How single sign-on to local resources works on Microsoft Entra joined devices – Microsoft Entra ID | Microsoft Learn.
- Recommendation: Deploy the Microsoft Entra Application Proxy to enable secure access for these applications.
-
- On-premises network shares: Users receive single sign-on through Microsoft Entra joined devices if the device has access to an on-premises domain controller. Learn how it works.
- Printers: You should deploy Universal Print to have a cloud-based print management solution with no local dependencies.
- On-premises applications: Use computer authentication: Devices joined to Microsoft Entra do not support on-premises applications that use computer authentication.
- Recommendation: Retire these applications and switch to more modern alternatives.
-
- Remote Desktop Services: After the Windows 10 2004 Update, users will be able to use a Remote Desktop connection on a Microsoft Entra registered device running Windows 10 or later with another Microsoft Entra joined device.
-
- RADIUS and Wi-Fi authentication: Currently, Microsoft Entra joined devices do not support RADIUS authentication using a local computer object and a certificate to connect to Wi-Fi access points, as RADIUS relies on the presence of a local computer object in this scenario. Alternatively, you can use Intune-pushed certificates or user credentials to authenticate to Wi-Fi.
-
-
- EntraID Hybrid Joined:
Planen der Bereitstellung Ihrer Microsoft Entra-Einbindung – Microsoft Entra ID | Microsoft Learn
| Microsoft Entra hybrid join | Description |
|---|---|
| Definition | Joined to on-premises Microsoft Windows Server Active Directory and Microsoft Entra ID requiring organizational account to sign in to the device |
| Primary audience | Suitable for hybrid organizations with existing on-premises Microsoft Windows Server Active Directory infrastructure |
| Applicable to all users in an organization | |
| Device ownership | Organization |
| Operating Systems | Windows 11 or Windows 10 except Home editions |
| Windows Server 2016, 2019, and 2022 | |
| Provisioning | Windows 11, Windows 10, Windows Server 2016/2019/2022 |
| Domain join by IT and autojoin via Microsoft Entra Connect or AD FS config | |
| Domain join by Windows Autopilot and autojoin via Microsoft Entra Connect or AD FS config | |
| Device sign in options | Organizational accounts using: |
| Password | |
| Passwordless options like Windows Hello for Business and FIDO2.0 security keys. | |
| Device management | Group Policy |
| Configuration Manager standalone or co-management with Microsoft Intune | |
| Key capabilities | single sign-on (SSO) to both cloud and on-premises resources |
| Conditional Access through Domain join or through Intune if co-managed | |
| Self-service Password Reset and Windows Hello PIN reset on lock screen |