Naming Conventions Intune & Entra ID etc.
Intune Policy Configuration
Platform – Set – Profile Type – Setting name [(optional info)] – Version
| Platform | Set | Profile Type | Setting name | optional info | Version |
| Indicator for platform type e.g. Win, macOS | Indictor profile set e.g. Default, Kiosk, SharedDevices, PAW | Indicator profile type e.g. Device restrictions, Custom | Indicator setting e.g. Edge Favorites, for Custom AreaName/PolicyName | Optional flag indicator e.g. test or work in progress | V1 Indicator version to keep track of changes |
Examples:
- Win Win – Default – Custom – DeliveryOptimization settings – V1 – Default – Custom – V1
- Win Win – Default – Authentication/AllowAadPasswordReset – V2
- Win – PAW – Custom – WiredNetwork/LanXML (test) – V1
- Win – SharedDevices – Custom – UserRights/DebugPrograms (piloting) – V1
- Win – Default – SCEP certificate – Device certificate settings – V3
- iOS – Kiosk – Device restrictions – Edge settings – V1
Conditional Access Policies
- A Sequence Number
- The cloud apps it applies to
- The response
- Who it applies to
- When it applies
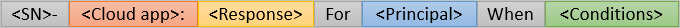
Example: A policy to require MFA for marketing users accessing the Dynamics CRP app from external networks might be:

Naming standards for emergency access controls
In addition to your active policies, implement disabled policies that act as secondary resilient access controls in outage or emergency scenarios. Your naming standard for the contingency policies should include:
- ENABLE IN EMERGENCY at the beginning to make the name stand out among the other policies.
- The name of disruption it should apply to.
- An ordering sequence number to help the administrator to know in which order policies should be enabled.
Example: The following name indicates that this policy is the first of four policies to enable if there’s an MFA disruption:
- EM01 – ENABLE IN EMERGENCY: MFA Disruption [1/4] – Exchange SharePoint: Require Microsoft Entra hybrid join For VIP users.
EntraID Groups
Microsoft 365 groups
for M365 groups you can en force a nimng policy:
Enforce a group naming policy in Microsoft Entra ID – Microsoft Entra ID | Microsoft Learn
EntraID Security Groups
Environment-Location-OperatingSystem-Purpose-Department-UserGroup-GroupType-[ProjectName]
Example:
- Prod-BER-Win10-MicrosoftEdgeBookmarks-IT-Exec-Dyn-[Alpha]
- UAT*-NY-MacOS-AppDeployment-Finance-Field-Stat-Beta
*UAT= User Acceptance testing
Special Group Names for Intune App Deployments:
APP-InstallType-OS-[Entitiy]-DepoymentType-AppName
Example:
- APP-DEPLOY-WIN10-USER-REQ-Firefox
- APP-Deploy-IOS-Available-Chrome
Autopilot
Device naming
the Out-Of the box solution brings only this Option :
- %SERIAL%: This placeholder is used to insert the device’s serial number into the name. For example, if your device’s serial number is
123456789, using%SERIAL%in the naming convention would result in a name likeDeviceName-123456789. - %RAND%: This placeholder is used to insert a random number into the name. You can specify the length of the random number by adding a number after
%RAND%, like%RAND:6%for a 6-digit random number. For example,%RAND:6%might result in a name likeDeviceName-987654.
Additional you can use user group tags in Autopilot:
But if you want more than this – and really want to have a nice Device niming here is a cool documentation for doing this:
More options for Autopilot Naming Convention
References:
Plan a Microsoft Entra Conditional Access deployment – Microsoft Entra ID | Microsoft Learn
